Security, GDPR, and IT Outsourcing: How to Get it Right?
Europe is now facing the wave of change in its data-protection laws. The new General Data Protection Regulation (GDPR) already took effect on May 25 in 2018. It is poised to regulate national data-protection laws and simplify compliance across the European Union. This regulation comes with significant changes compared to the Data Protection Directive 95/46/EC. It will provide businesses with a clearer legal structure and ensure that personal data is protected against misuse and theft.
According to IBM, there has been a 29% increase in the total cost of data breaches since 2013. Nevertheless, information governance reduces losses by $1 million annually, so there’s never been a better time to audit and control your data.
How GDPR is going to affect businesses in general is one thing. We are more interested in how it will impact outsourcing arrangements and IT outsourcing industry in particular. One thing is clear. Software development vendors should take information security seriously and take consistent steps to comply with GDPR and other security regulations.
Drawing on our industry observations and regulatory experience, we have highlighted a number of actions that contribute to a successful GDPR effort. So what does the new GDPR entail? How to comply with its requirements? And how does compliance with GDPR stimulate outsourcing vendors to rethink their data protection policies and processes?
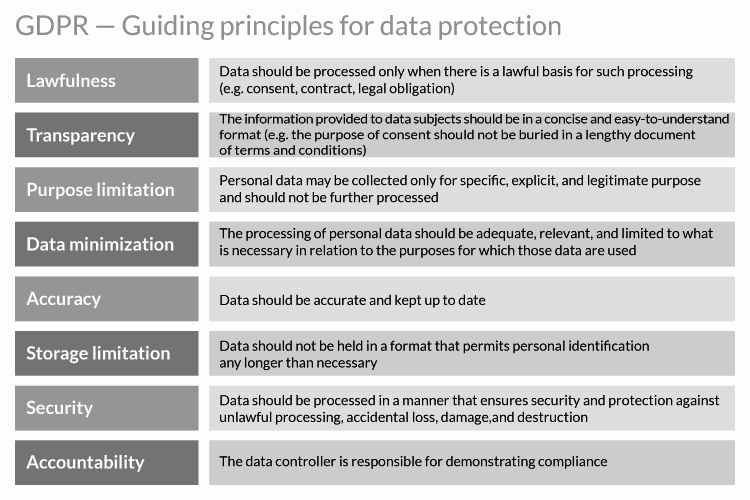
GDPR in a nutshell
The General Data Protection Regulation is a directive established by the European Union to protect individuals’ personal information. The regulation became in force May 25, 2018, and replaced the EU’s 1995 Data Protection Directive. The new GDPR is applicable to all organizations that collect or process the personal data of EU citizens or residents.
Under its regulations, companies are required to implement a number of initiatives for safeguarding data, as well as technical & organizational measures to protect data and the individuals’ privacy rights. Companies are also required to ensure systems and procedures are able to properly test, monitor and measure data security. Thus companies need to be extremely aware of these changes as they may face strict fines in the cases of non-compliance. Any failure may cause financial penalties up to $22 million or up to 4% of annual revenues.
GDPR also imposes obligations on controllers—individuals or the company which determines the purposes and means of the personal data processing. If the business decides to outsource some of its functions, there is a possibility that personal data will need to be transferred to the outsourcing vendor as part of that transaction. In most cases, the business transferring its data will remain the controller which means it will be responsible under the law for how those data are processed.
GDPR compliance
Key steps outsourcing vendors must make towards successful GDPR compliance
In order to successfully prepare for GDPR, software development vendors need to establish a solid foundation for achieving compliance. Most critically, all existing data stores and new processes under GDPR must be thoroughly examined to effectively execute data security measures. On the whole, compliance with GDPR includes 6 major steps:
1. Raise GDPR Awareness
An awareness of GDPR is the first requirement. Any trusted outsourcing vendor must develop a full understanding of what GDPR entails, given the specifics of the organization’s business practices. It is vital to know that GDPR applies to any organization in the world as long as it retains any information where EU citizens are the data subjects. Key people in IT outsourcing companies should understand the impact of GDPR and the areas of the business that will be most affected when it comes into effect. Raising GDPR awareness is especially crucial for larger companies since they have more channels for acquiring and storing customer data.
2. Perform a gap analysis
Another important step your outsourcing vendor should take is auditing existing processes to perform a gap analysis. This will further define where new procedures and specialists are needed to improve practices and achieve GDPR compliance. This will also help determine what type of technology is required to fill any gaps regarding data security, data auditing, and data privacy needs. This may also require new technological solutions. Thus any reputable IT provider must identify and address any vulnerabilities or blind spots.
3. Create a data register
As soon as you potential business partner has a clear vision about its readiness to meet the regulatory requirements, he needs to keep a record of the process. This should be done through creating a Data Register.
Every European country has a Data Protection Association (DPA), that will be responsible for enforcing GDPR. This organization will judge whether a business has been compliant when determining any potential penalties for being breached. In case a breach occurs, your outsourcing vendor should be able to show the DPA its progress towards compliance through its Data Register. If the company doesn’t provide evidence that it even started the process, the DPA may enforce a fine. It may reach an amount of 2-4% of the company’s turnover, depending on the sensitivity of the data being breached.
4. Evaluate existing technology
Examining organization’s technology requirements is vital for understanding which of the current solutions need to be upgraded or replaced. For example, in some IT companies such departments as legal, information security, HR, etc. may have systems that are transferring protected data between countries. The operations of these departments must be thoroughly investigated – especially when it comes to the flow of data and how it is used. A complete understanding of these technologies may allow leveraging existing solutions for GDPR compliance. Moreover, it may reveal all technology gaps that need to be filled.
5. Analyze potential risks
The next stage of GDPR compliance is to assess and document any risks and vulnerabilities. It is vital for established IT outsourcing companies to keep a roadmap document that ensures the security level is appropriate to the risk. This also includes encrypting and pseudonymisation of personal data in order to mask the most identifying fields within data records. Any reliable IT vendor must embed the golden principles of infosecurity, namely confidentiality, integrity and availability of data processing systems and services. Therefore, in case of a breach or technical incident, he will be able to restore the availability of personal data in a timely manner.
6. Continuous testing
Finally, after establishing the above-mentioned steps, it is essential to receive continual insights that can inform process improvements. Any reliable business partner must be certain that best practices are still actual and protected data never passes through systems that haven’t been carefully secured. Thus companies are expected to set up a process for regularly assessing and testing security practices. Theirincident response processes should undergo periodic testing and be the subject of ongoing reporting. In such way, your outsourcing partner will remain full prepared for any breaches.
What is Intellica doing about the GDPR?
Intellica infosec team is allocating internal resources and conducting an audit for GDPR compliance. We are fully committed to achieving compliance with the GDPR prior to the regulation’s effective date. In our GDPR Roadmap we’ve included the following procedures:
Thoroughly researching all areas impacted by GDPR;
Setting clear guidelines and well-controlled methods to ensure the company is able to quickly respond to data breaches;
Ensuring the company’s privacy policy and guidelines are transparent and easily accessible;
Establishing regular monitoring, inspection, and judgment processing procedures to minimize data storage, data processing, and protective measures;
Pseudonymizing, minimizing and encrypting personal data both at rest and in transit;
Implementing the required changes/improvements to our internal processes and procedures required to achieve and maintain GDPR compliance;
Thoroughly testing all of our changes to verify and validate compliance with GDPR
Afterword
On the whole, GDPR will alter business requirements for companies that possess personal information related to EU residents. It is designed to harmonize their data privacy laws and give greater protection and rights to individuals. To achieve GDPR compliance, outsourcing vendors must introduce new important steps and ensure that personal data is protected against misuse and theft. They should conduct audits and invest in solutions for data loss prevention to adhere to all guidelines. Therefore, before entering into an outsourcing agreement, make sure your IT provider has a well-defined security policy and complies with GDPR requirements. In such case, you may be sure that your data is kept safe and secure in the long run.